Splunk App for Infrastructure
Greetings everyone,
Here I would like to cover basics of another cool app which you can have with your current Splunk Enterprise license.
It is Splunk App for Infrastructure – SAI shortly. Please review System Requirements before installing the app. One of the critical requirements I would like put some more emphasize is Splunk Add-on for Infrastructure which deals with index creation and other stuff.
Once you have installed it, you are required to add entities which are the targets that you would like to monitor.
- Linux/Unix
- AWS
- Windows
- OSX
- Kubernetes
- OpenShift
- VMware vSphere
At the time I am composing the post, I can add above integration. For each and every integration you have to provide different type of inputs. Once you have provided the required inputs for the particular integration, it will bake you an installation script which I found fantastically easy 🙂
Here are two samples for Windows and Linux platforms.
Windows
$env:SPLUNK_URL="10.0.0.4" ; $env:RECEIVER_PORT="30002" ; $env:DIMENSIONS="role::`"client`"" ; $env:SPLUNK_HOME="$env:programfiles\SplunkUniversalForwarder" ; $env:METRICS="cpu,physical_disk,network,memory,system,process,logical_disk"; $env:PER_CPU="true"; $env:LOG_SOURCES="`$SPLUNK_HOME\var\log\splunk\*.log*%uf,Application%WinEventLog,Security%WinEventLog,System%WinEventLog,Forwarded Events%WinEventLog,Setup%WinEventLog"; $web=New-Object Net.WebClient; $path=Convert-Path .; [System.Net.ServicePointManager]::ServerCertificateValidationCallback={$true}; [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 ; $files="install_uf.ps1","install_uf_script.ps1"; Foreach($file in $files) { $web.DownloadFile("https://10.0.0.4:8000/static/app/splunk_app_infrastructure/windows_scripts/$file",$path+"\$file")}; [System.Net.ServicePointManager]::ServerCertificateValidationCallback = $null; if ($?) { .\install_uf.ps1 }Linux
export SPLUNK_URL=10.0.0.4 && export HEC_PORT=8088 && export RECEIVER_PORT=30002 && export INSTALL_LOCATION=/opt/ && export HEC_TOKEN=65c69f79-eeee-48ab-5555-8fc631a22064 && export SAI_ENABLE_DOCKER= && export DIMENSIONS=role:"ubuntu" METRIC_TYPES=cpu,uptime,df,disk,interface,load,memory,processmon METRIC_OPTS=cpu.by_cpu LOG_SOURCES=/etc/collectd/collectd.log%collectd,\$SPLUNK_HOME/var/log/splunk/*.log*%uf,/var/log/syslog%syslog,/var/log/daemon.log%syslog,/var/log/auth.log%syslog AUTHENTICATED_INSTALL=Yes && export INSTALL_LOCATION=/opt/ && wget --no-check-certificate https://10.0.0.4:8000/static/app/splunk_app_infrastructure/unix_agent/unix-agent.tgz && tar -xzf unix-agent.tgz || gunzip -c unix-agent.tgz | tar xvf - && cd unix-agent && bash install_uf.sh && bash install_agent.sh && cd .. && rm -rf unix-agent && rm -rf unix-agent.tgz—DON’T COPY/PASTE ABOVE ONES—
You have to prepare similar ones appropriate you your environment. I installed the forwarders on 3 target platform by installation scripts.
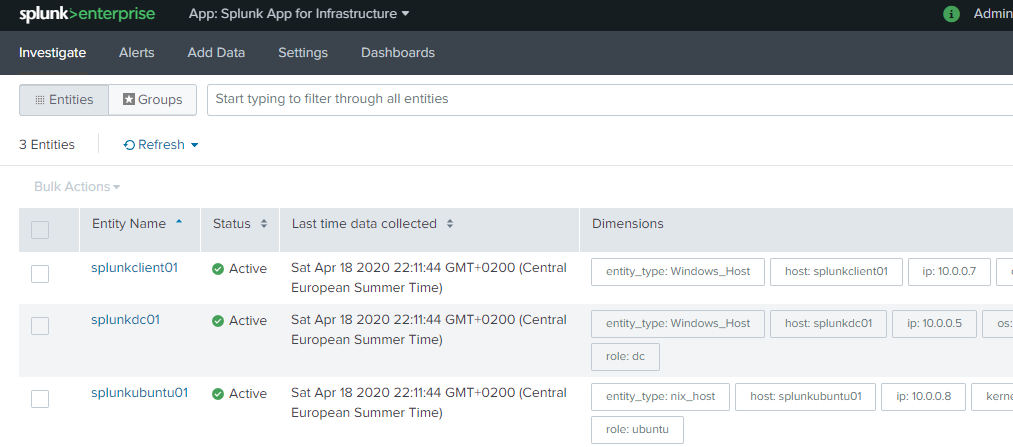
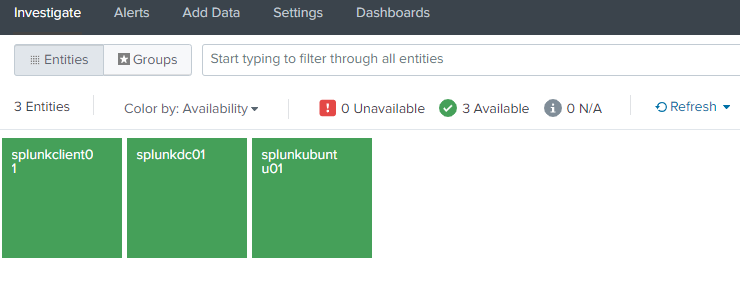
You can also have tile view like below.
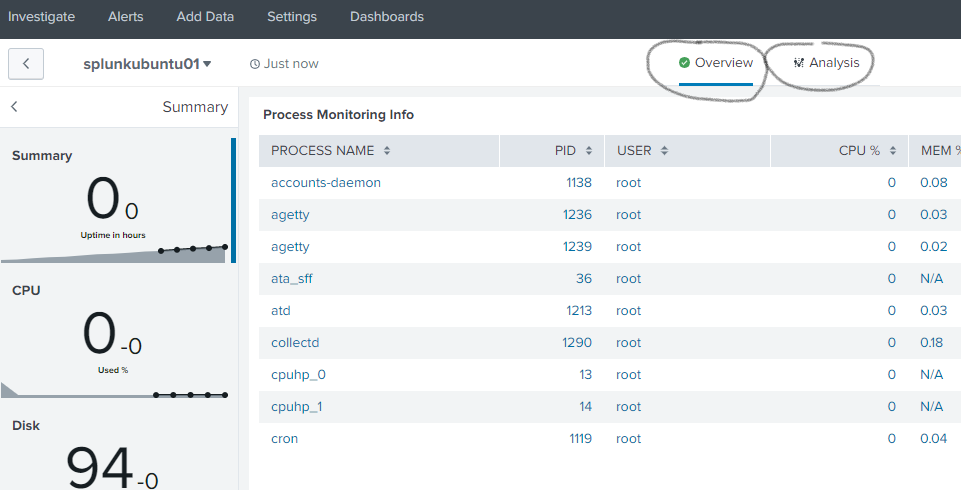
Once you have clicked one of the tiles , you will reach out to details for analysis as shown below.
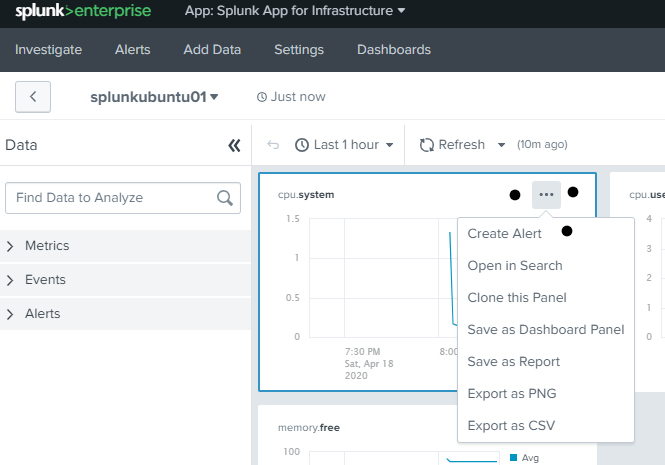
You can create alerts under Analysis menu for a particular performance counter like CPU idle time , free disk space percentage , etc and you can add slack(web hook),email and some others as notification channel.
Here is sample notifications I set with my slack workspace.
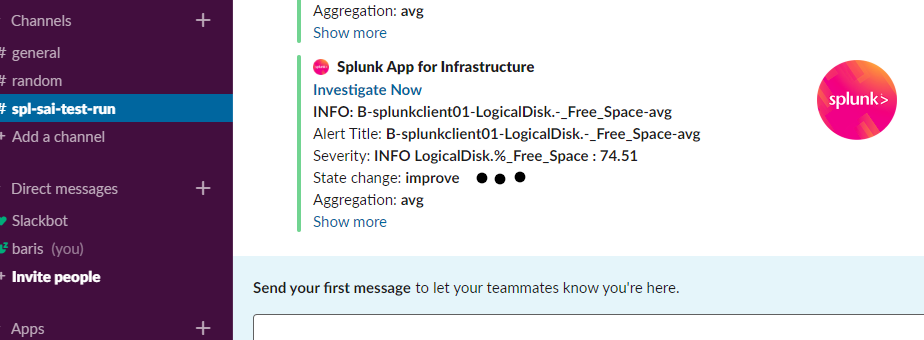
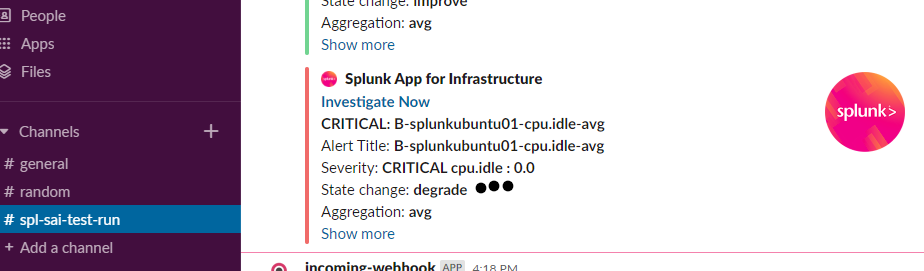
For more you need to explorer 🙂 But if you ask what would be the next step is, I would say integrating this app with Splunk ITSI.
Useful links:
https://www.splunk.com/en_us/resources/videos/splunk-app-for-infrastructure-demo.html
https://splunkbase.splunk.com/app/3975/#/details
https://docs.splunk.com/Documentation/InfraApp/2.0.3/Admin/HEC
https://docs.splunk.com/Documentation/InfraApp/2.0.3/Install/SystemRequirements